Whitepapers
-
The Developer’s Guide to Relationship-based Access Control
![]()
Start implementing Relationship-based access control. Your databases likely contain a network of entities and their relationships already.
-
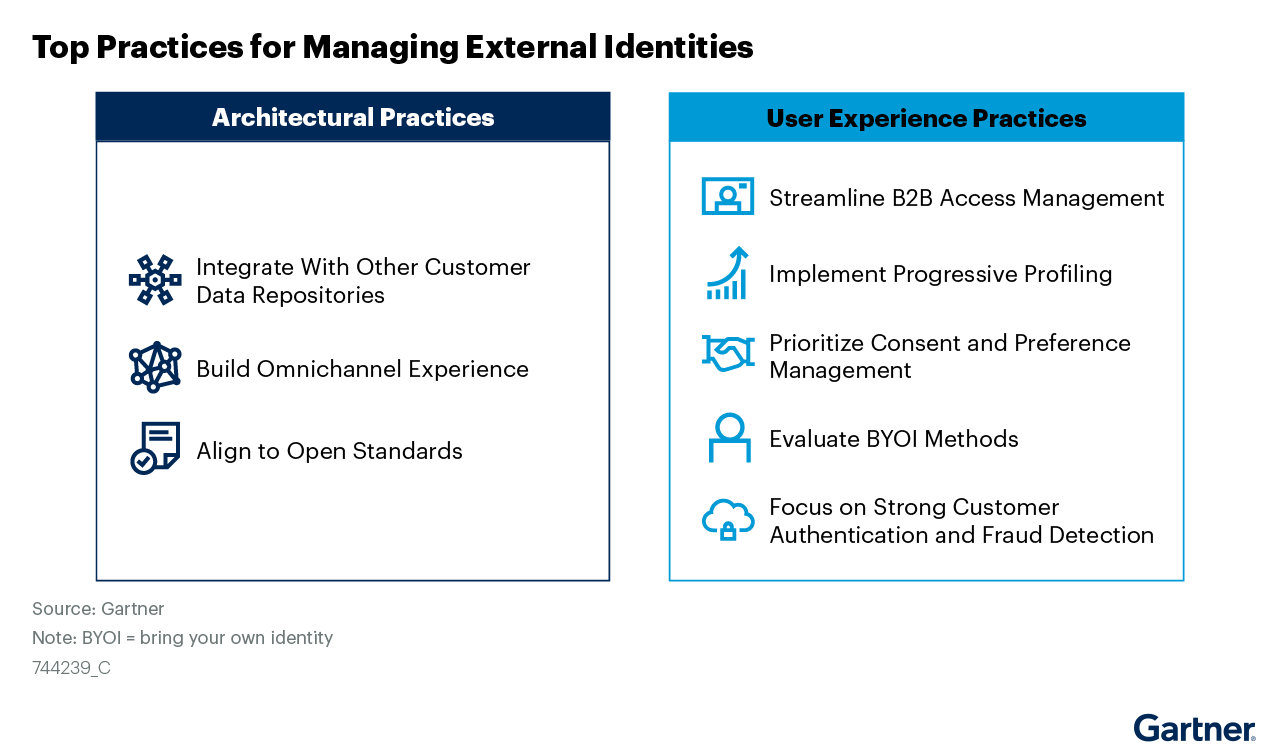
Managing External Identities Using a Customer Identity and Access Management Tool
![]()
Use this Gartner® research to learn how to implement a cohesive customer access management solution that lets customers, partners, and gig workers access your applications.
-
Nine Common Access Management Misconceptions Debunked
![]()
It’s about time to clear up some common misconceptions about access management. Here’s a list of the traditional views that no longer hold true.
-
Consumers Value Sharing. Security Will No Longer Stand in Their Way.
![]()
Authorization management has evolved to meet consumer sharing expectations and habits that they have acquired through social media, while ensuring security and privacy.
-
How authorization technology will revolutionize the way we collaborate
![ecosystem access]()
Advanced access control systems let stakeholders, both inside and outside the organization, conveniently share information, knowledge and functionalities.
-
Monetize a Loyal Audience without Alienating more Casual Viewers who want to Sample Content
![]()
How publishers & broadcasters use advanced CIAM technology to grow and engage audiences and convert casual viewers.
-
Scaled Access ROI
![]()
Whether you want to replace a homegrown solution or an existing vendor, the investment you make in us will be a good one.
-
Accelerating Secure OAuth 2.0 Compliant Advanced Authorization: Authlete & Scaled Access
![]()
Read how Authlete and Scaled Access’s combined solution enables organizations to build and operate OAuth 2.0 compliant authorization servers
-
Data Protection:
From Obligation to Opportunity![]()
GDPR leverages significant opportunities in terms of engagement and customer retention.
-
10 Reasons to Buy an Access Management Tool Rather Than Build
![]()
Think cost is the important factor? Think again.
-
Sharing Confidential Data Doesn’t Require Sharing Credentials
![]()
Read how advanced authorization platforms provide an alternative to credential sharing.
-
Why Consent Management is a Priority During Your Application Build
![]()
Learn why consent management is a vital component of your applications.