Managing External Identities Using a Customer Identity and Access Management Tool
Use this Gartner® research to learn how to implement a cohesive customer identity and access management solution that lets customers, distributors, dealers, partners, and gig workers access a potentially wide range of applications.
The Scaled Access platform is designed to offer access to external identities, providing built-in advanced features such as delegated administration & fine-grained access control.
Any personal data you provide is collected and processed by Scaled Access, as a controller, in order to service your submission.
Read more in our Privacy Policy.
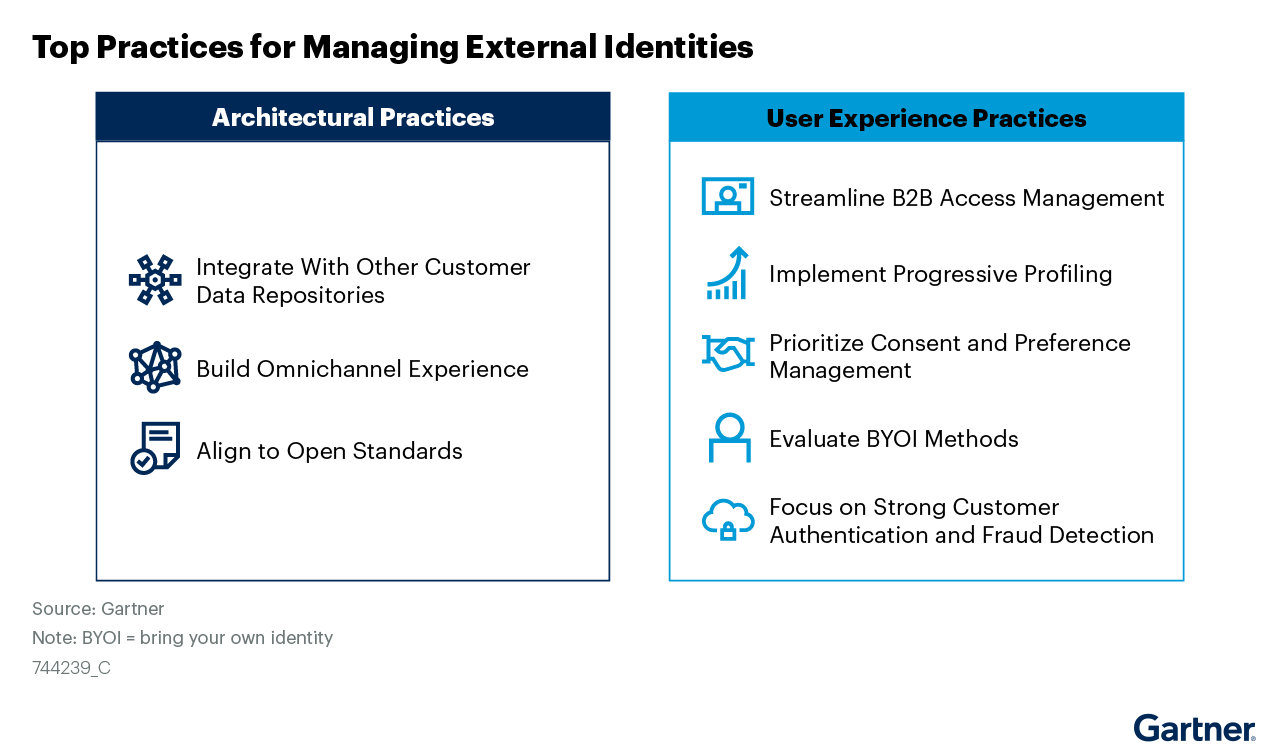
Main Takeaways:
- “Enhance the user experience of external identities by choosing CIAM tools that support both B2B and B2C capabilities and include delegated administration, delegation of consent, and strong customer authentication as differentiators.
- B2B needs can increasingly be supported by the same CIAM tools used for B2C
- Fine-grained access control — for example, the ability to grant a user access to some, but not all, data in a specific application.
- B2B use cases can require access rights to vary depending on the specifics of the business relationship”
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Scaled Access.
Gartner, Managing External Identities Using a Customer Identity and Access Management Tool, November 11, 2021, Henrique Teixeira, Abhyuday Data, Michael Kelley.
GARTNER and Hype Cycle are registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner © disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Other Whitepapers

The Developer’s Guide to Relationship-based Access Control
Start implementing Relationship-based access control. Your databases likely contain a network of entities and their relationships already.
Whitepapers

Nine Common Access Management Misconceptions Debunked
It’s about time to clear up some common misconceptions about access management. Here’s a list of the traditional views that no longer hold true.
Whitepapers

Consumers Value Sharing. Security Will No Longer Stand in Their Way.
Authorization management has evolved to meet consumer sharing expectations and habits that they have acquired through social media, while ensuring security and privacy.
Whitepapers

How authorization technology will revolutionize the way we collaborate
Advanced access control systems let stakeholders, both inside and outside the organization, conveniently share information, knowledge and functionalities.
Whitepapers

Monetize a Loyal Audience without Alienating more Casual Viewers who want to Sample Content
How publishers & broadcasters use advanced CIAM technology to grow and engage audiences and convert casual viewers.
Whitepapers

Scaled Access ROI
Whether you want to replace a homegrown solution or an existing vendor, the investment you make in us will be a good one.
Whitepapers

Accelerating Secure OAuth 2.0 Compliant Advanced Authorization: Authlete & Scaled Access
Read how Authlete and Scaled Access’s combined solution enables organizations to build and operate OAuth 2.0 compliant authorization servers
Whitepapers

Data Protection:
From Obligation to Opportunity
GDPR leverages significant opportunities in terms of engagement and customer retention.
Whitepapers

10 Reasons to Buy an Access Management Tool Rather Than Build
Think cost is the important factor? Think again.
Whitepapers

Sharing Confidential Data Doesn’t Require Sharing Credentials
Read how advanced authorization platforms provide an alternative to credential sharing.

